In iOS 17.4, iPadOS 17.4, and macOS 14.4 Sonoma, Apple enhanced its Podcasts app to include transcripts of all podcasts in the Apple Podcasts catalog as long as they’re in English, French, German, or Spanish. (It doesn’t translate from one language to another.) Much like song lyrics in the Music app—open it by tapping the dialog button in the player—the …
Tips for Working with Mac Display Resolutions
You can change the resolution of your Mac’s screen—how many pixels appear—to make text and graphics larger and easier to see or smaller to fit more content onscreen. In System Settings > Displays, Apple shows thumbnails for five likely possibilities. Hover the pointer over a thumbnail to see its numeric resolution underneath. If you prefer the traditional list of numeric …
Want an Event List in Apple’s Calendar App? Try This Trick
Along with day, week, month, and year views, most calendar apps offer the option of a simple chronological list of events, which can be a handy way to see what’s coming up. Apple’s Calendar app on the Mac is unfortunately not among those apps. However, there is a trick you can use to get it to show all your upcoming …
Looking for Apple Manuals? Check the New Documentation Site
Apple publishes a multitude of manuals and tons of technical documentation for its products on its support site, but until recently, it could be challenging to find something specific because the search engine on Apple’s site is poor. For a better path into Apple’s online support materials, check out the company’s new Documentation site, which brings together manuals, specs, and …
How to Sync Your Text Messages across All Your Apple Devices
Although many of us think of Messages as an iPhone app, Apple’s platform integration lets you read and reply to conversations in Messages on other Apple devices, including the Mac and iPad. All your devices must have the correct settings to make this work reliably. We regularly hear from users who don’t see all their messages on all their devices. …
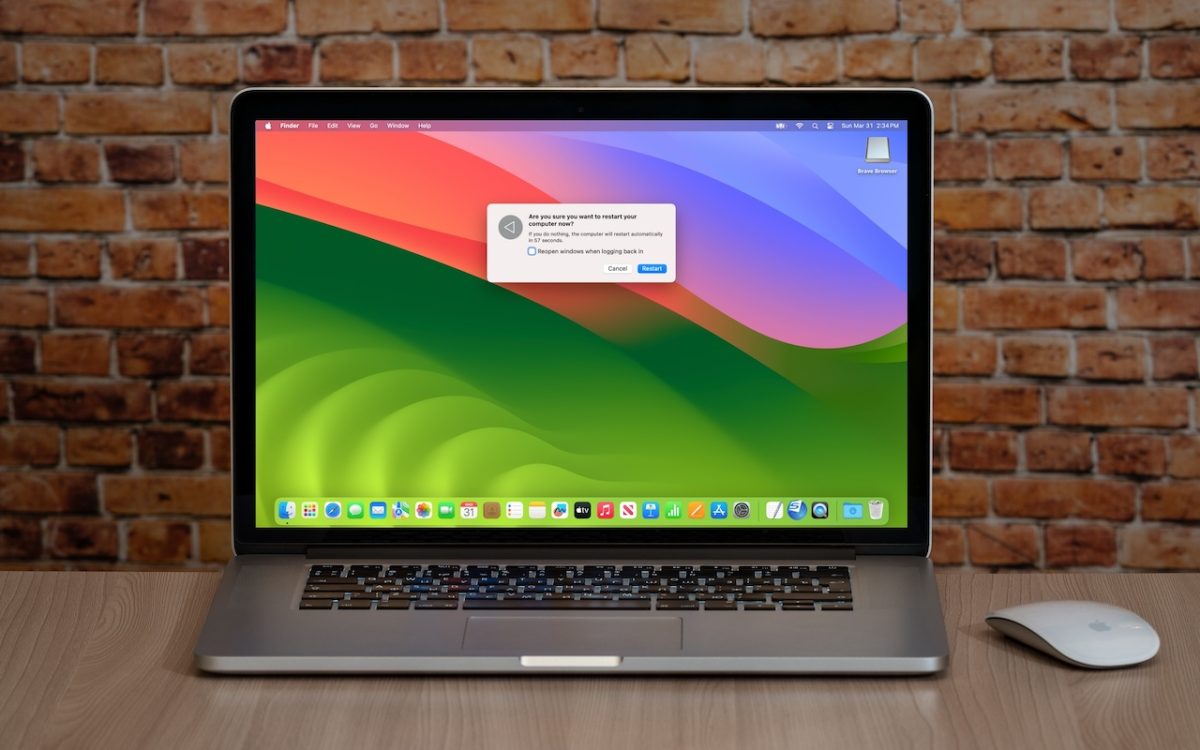
Six Reasons Why You Should Restart Your Mac Periodically
Long ago, before macOS was as stable as it is today, Mac users restarted their Macs regularly. Back then, Macs couldn’t sleep, either, so it was common for users to shut down at the end of the day and start up the next morning, effectively restarting daily. With modern Macs using the barest trickle of power in sleep and both …
SPF, DKIM, and DMARC: What They Are and Why You Need Them
The ease of sending and receiving email makes it an attractive way to run scams like phishing attacks. One telltale mark of a phishing attack is the sender’s address not matching their purported domain; attacks that appear to come from legitimate email addresses are much more likely to fool the victim. You can protect your organization’s email accounts from being …
Take Advantage of the Reference Library in Your Mac
You may be used to Mac apps using red underlines to mark misspelled words, but did you know that macOS has also long included a fully featured Dictionary app? It provides quick access to definitions and synonyms in the New Oxford American Dictionary and the Oxford American Writer’s Thesaurus, along with definitions of Apple-specific words like AirDrop and Apple ProRes …
Apple Announces New MacBook Air Lineup with M3 Chip
In November 2023, Apple unveiled the M3 chip in new versions of the 24-inch iMac and MacBook Pro, causing speculation about when other Mac models would be updated to match. If you’ve been longing for a MacBook Air with an M3 chip, your wait is over. (And we expect Apple to update the Mac mini soon.) Apple has now announced …
Did You Know Text Entry Boxes in Web Browsers Are Easy to Expand?
Have you ever noticed the shading in the corner of text area fields in Safari, Chrome, Firefox, and most other Mac Web browsers? These “handles” let you resize the field—always vertically and sometimes horizontally. That’s handy when the website designer has provided only a small text box and you want to enter more text than will fit. Just drag the …